What’s that lurking in the shadows?
Staff using unapproved apps without consulting IT?
Shadow IT happens much more than many leaders know, but is it that bad? Surely, rules exist for us to break them, and there must be digital change management benefits to thinking outside the box when choosing apps to use at work, right?
Well, yes and no.
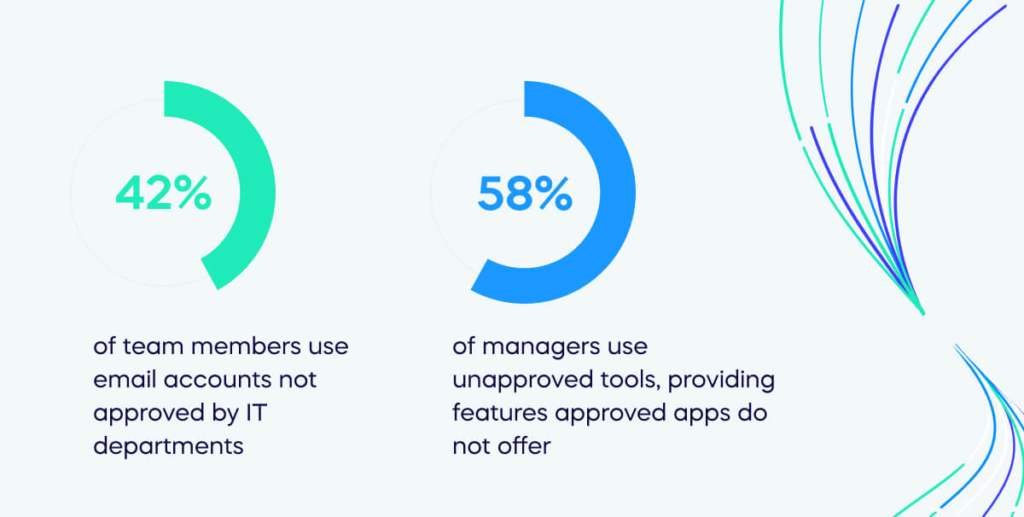
42% of team members use email accounts not approved by IT departments, and 58% of managers use unapproved tools, providing features approved apps do not offer.
Yet, one-third of all data breaches result from shadow IT tools (cited above), and change leadership is not always aware.
To help you understand what shadow IT is, how to identify shadow IT, and how to remain safe while using it, we will explore the following topics:
- What is shadow IT?
- Why is shadow IT important?
- What is a shadow IT application, and what types are there?
- What does shadow IT look like in 2023?
- Is shadow IT a threat?
- Is shadow IT a good thing?
- What is an example of shadow IT in business?
What is shadow IT?
Shadow IT is utilizing IT systems, devices, software, apps, and cloud services without official approval from the IT department. Its prevalence surged due to embracing cloud-based apps and services.
Although shadow IT has the potential to boost employee productivity and foster innovation, it can also pose significant security threats to your organization, including data breaches, possible breaches of compliance, and other concerns.
Why is shadow IT important?
Shadow IT becomes an option for employees when the required solutions are unavailable, or they aim to bypass established business limitations.
In numerous enterprises, staff see the IT team as a hindrance rather than an ally. Alternatively, stringent corporate regulations hinder meaningful progress.
Welcoming Shadow IT enables you to equip employees with the necessary tools for their daily responsibilities. Consequently, they devote less time to seeking alternatives and more time to achieving tasks.
However, there are risks associated with shadow IT, which makes it an essential part of your IT strategy to consider using it or not.
What is a shadow IT application, and what types are there?
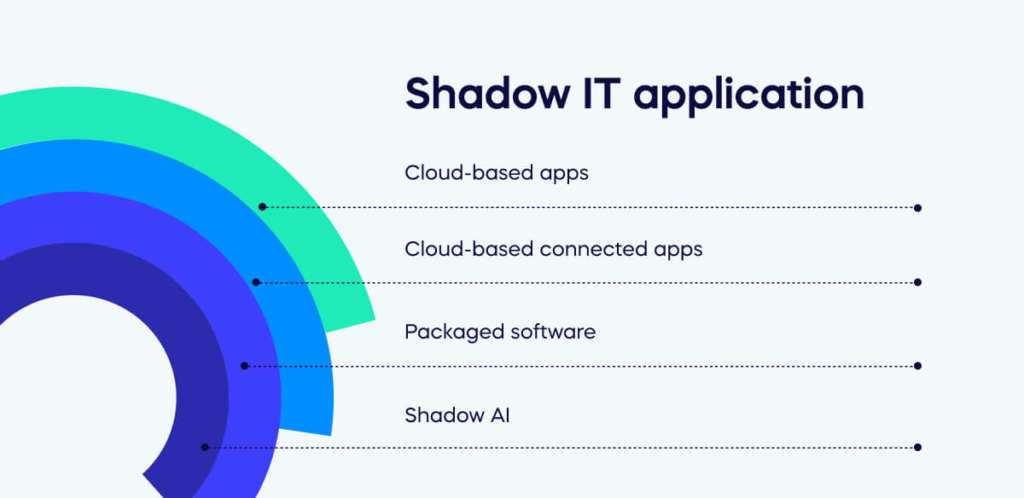
Any application a department or end user adopts for business without IT group involvement is shadow IT. These apps fit into three main types:
1. Cloud-based apps accessed directly from the corporate network.
2. Cloud-based connected apps accessed via an OAuth token (using credentials from a core SaaS app like Microsoft Office 365 or Google’s G Suite).
3. Packaged software purchased by a department or end-user and installed on the system. This kind is less common due to the rise of SaaS solutions.
4. Shadow AI includes generative AI tools like ChatGPT that staff use on mobile devices or desktop to automate tasks without IT approval.
Be aware of what shadow IT applications look like to help you identify and manage them.
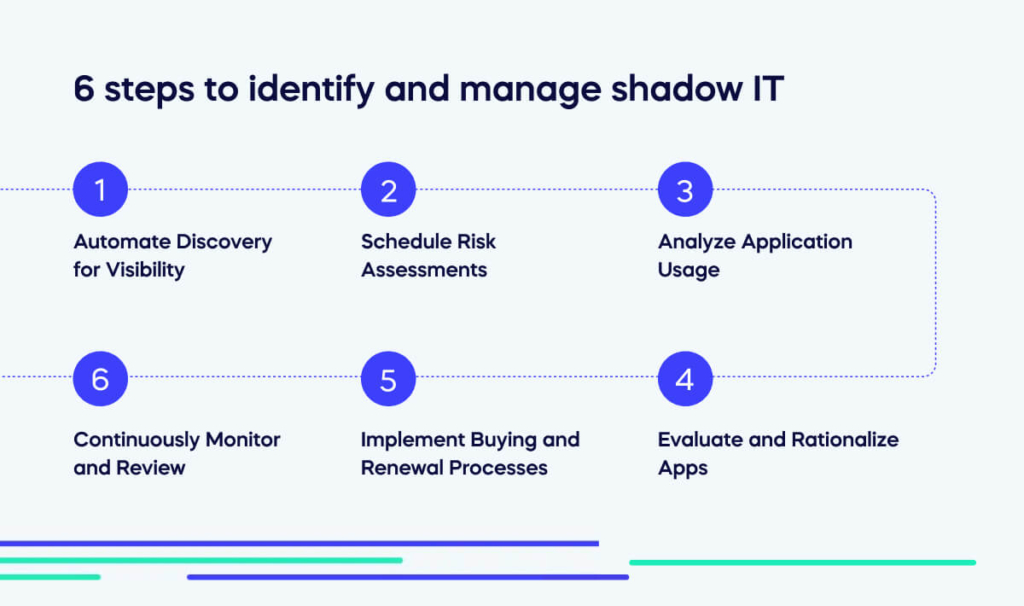
6 steps to identify and manage shadow IT
Embracing a cloud-first approach increases encounters with shadow IT. However, you can address challenges and costs effectively. Proper shadow IT management is crucial to harness advantages while mitigating risks.
Below is a shadow IT governance process for discovering, managing, and auditing unknown applications used by employees:
1. Automate Discovery for Visibility
Discover all software in your portfolio through automated SaaS management, Application Portfolio Management (APM) platforms, or surveys.
Manual methods are inadequate for larger organizations—store app details like owner, licenses, and spending to enhance accountability.
2. Schedule Risk Assessments
Assess compliance, security certifications, and corporate data storage of apps. Evaluate regulatory and business risks. Prioritize actions based on security breaches, certifications, and future value.
3. Analyze Application Usage
Track usage patterns via integrations and APIs. Identify underutilized apps. Begin with high-cost services, measure utilization, and categorize and compare usage.
4. Evaluate and Rationalize Apps
Rationalize apps based on need, user, and duration. Optimize or retire unused software. Categorize apps by importance, consider renewal dates, and sunset duplicative tools.
5. Implement Buying and Renewal Processes
Develop a process for buying apps with business cases. Extend renewals, establish a renewal calendar, and communicate strategies to employees.
6. Continuously Monitor and Review
Automate monitoring to ensure rationalization and compliance. Regular reviews prevent data exposure, ensure policy compliance, and manage software costs.
This six-step process empowers organizations to navigate the challenges of shadow IT while reaping its benefits. However, it is limited as organizations cannot monitor specific devices such as employee’s personal devices or their personal Dropbox account.
Focus on what you can monitor, such as critical systems, and bear in mind that there are limitations to specific security measures.
Solve specific measures with open dialogue and encouraging best practices linking back to employees choosing to self-monitor and avoiding shadow IT where possible.
Is shadow IT a threat?
IT and security units must gain visibility into the employed applications and their associated hazards.
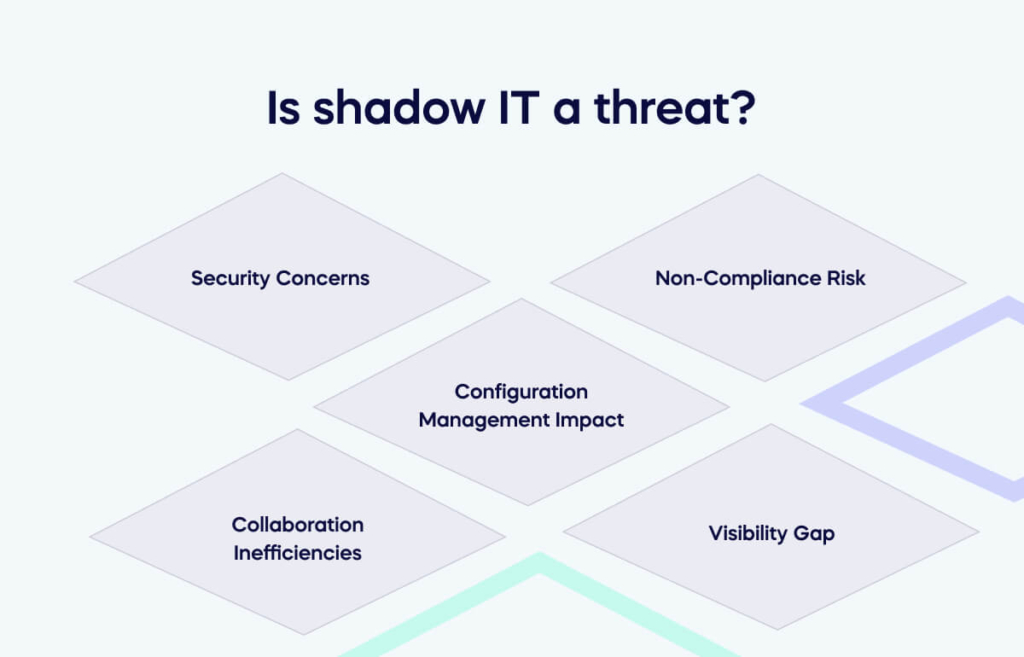
Security Concerns
Over half of organizations overlook shadow IT in their threat assessments, introducing security gaps. While some apps are benign, others may facilitate security risks like data leaks. Hence, IT should be informed about apps used for file sharing and more.
Non-Compliance Risk
Organizations safeguard clients, customers, and partners to adhere to compliance regulations mandated by governments. Shadow IT-triggered non-compliance could lead to hefty fines if unauthorized software endangers sensitive data confidentiality.
Configuration Management Impact
IT strives to establish seamless workflows via configuration management databases (CMDBs). Being off the radar, Shadow IT disrupts CMDB-backed systems due to its unrecognized existence.
Collaboration Inefficiencies
Teams relying on disparate apps hinder cross-functional collaboration. For instance, if one team uses Google Drive and another uses Dropbox, file handling becomes convoluted.
Visibility Gap
True to its name, shadow IT eludes IT departments. Though SaaS apps are compact, they can strain bandwidth or malfunction. Unrecognized broken apps impede quick fixes or solutions.
Is shadow IT a good thing?
There are four benefits of shadow IT for your business when you manage it effectively:
1. Empowers Employee Innovation
Shadow IT arises when users seek alternatives due to delays in IT application development.
IT can properly equip an agile workforce with tools to craft their solutions, giving them control over data and access without relying on IT requests.
This action fosters a shift towards employee-driven solutions and innovation.
2. Aligned Solutions with Business Needs
Traditional requests to IT often lead to miscommunication and misaligned solutions. Shadow IT eliminates this risk by allowing users to find or build solutions that closely match their objectives.
This approach emphasizes solution appropriateness, alignment, and delivery speed.
3. Boosts Productivity and Removes Obstacles
Shadow IT emerges as employees seek solutions when IT barriers or strict corporate policies hinder them.
By embracing Shadow IT, employees gain tools for everyday tasks, reducing time spent on workarounds and increasing productivity. This initiative reflects employee efficiency and ownership.
4. Relieves IT Department Burden
IT departments often face heavy workloads, managing technology and handling various tasks. Embracing Shadow IT means granting users access to approved solutions or tools for self-creation.
Doing so eases the IT department’s load, enabling them to focus on mission-critical responsibilities.
What examples of shadow IT exist in business?
Many SaaS applications acquired by individuals leading to shadow IT typically fall within three main categories: productivity, communication, and collaboration.
With a continuous influx of new providers and applications offering diverse features, employees opt for apps that best match their needs and update software as they deem appropriate.
The subsequent list offers examples of typical shadow IT applications.
Productivity
Frequently, these apps revolve around enhanced project management, such as Trello or Hive, enabling employees to assign tasks and monitor time and progress.
Other productivity apps focus on social media management, like Hootsuite, or aiding employees in assessing written output quality, like Grammarly.
Communication
Communication tools have gained paramount significance due to the rise in remote work opportunities.
SaaS applications like Slack facilitate seamless communication, while video conferencing apps like Zoom or Webex assist remote teams in conducting video conferences and facilitating screen sharing.
Collaboration
Given the limitations of emailing large attachments, most teams resort to different file-sharing tools like Dropbox or OneDrive for file uploads and sharing.
Naturally, many SaaS tools exist for collaborative work within project management. Prime examples include business leaders using Google Docs or apps to streamline workflows, incorporate discussion boards, and offer real-time notifications.
In terms of hardware, typical shadow IT encompasses items such as servers, PCs, personal laptops, tablets, smartphones, and hard drives.
Minimize shadow IT risks with a DAP
In the ever-evolving landscape of IT, transparent communication remains a pivotal strategy to mitigate shadow IT risks effectively.
Organizations must recognize the potential of shadow IT to empower innovation while acknowledging its inherent security and compliance vulnerabilities. The best way to do this is by using the in-app guidance and personalized training capabilities of a DAP.
By using a DAP for proactive dialogue, informed decision-making, and collaborative problem-solving, enterprises can balance enabling innovation and safeguarding data integrity, thus steering clear of the pitfalls associated with shadow IT.

